- MPX 5900
- MPX/SDX 8900
- MPX/SDX 9100
- MPX/SDX 15000
- MPX/SDX 15000-50G
- MPX/SDX 16000
- MPX/SDX 26000
- MPX/SDX 26000-50S
- MPX/SDX 26000-100G
- Software-only support for the TLSv1.3 protocol is available on all other NetScaler MPX and SDX appliances except NetScaler FIPS appliances.
sh hardware Platform: NSMPX-22000 16*CPU+24*IX+12*E1K+2*E1K+4*CVM N3 2200100 Manufactured on: 8/19/2013 CPU: 2900MHZ Host Id: 1006665862 Serial no: ENUK6298FT Encoded serial no: ENUK6298FT
- To display information about the cipher suites bound by default at the front end (to a virtual server), type: sh cipher DEFAULT
- To display information about the cipher suites bound by default at the back end (to a service), type: sh cipher DEFAULT_BACKEND
- To display information about all the cipher groups (aliases) defined on the appliance, type: sh cipher
- To display information about all the cipher suites that are part of a specific cipher group, type: sh cipher . For example, sh cipher ECDHE.
The following links list the cipher suites supported on different NetScaler platforms and on external hardware security modules (HSMs):
- NetScaler MPX/SDX Intel Lewisburg appliance: Cipher support on a NetScaler MPX/SDX Intel Lewisburg SSL chip based appliance
- NetScaler MPX/SDX (N3) appliance: Cipher support on a NetScaler MPX/SDX (N3) appliance
- NetScaler MPX/SDX Intel Coleto appliance: Cipher support on a NetScaler MPX/SDX Intel Coleto SSL chip-based appliance
- NetScaler VPX appliance: Cipher support on a NetScaler VPX appliance
- NetScaler MPX/SDX 14000 FIPS appliance: Cipher support on a NetScaler MPX/SDX 14000 FIPS appliance
- External HSM (Thales/Safenet): Cipher supported on an External HSM (Thales/Safenet)
- NetScaler VPX FIPS and MPX FIPS appliances: Cipher support on NetScaler VPX FIPS and MPX FIPS appliances
Table1 - Support on virtual server/frontend service/internal service:
| Protocol/Platform | MPX/SDX (N2) | MPX/SDX (N3) | VPX | MPX/SDX 14000** FIPS | MPX 5900/8900 MPX 15000-50G MPX 26000-100G |
|---|---|---|---|---|---|
| TLS 1.3 | NA | 14.1 all builds | 14.1 all builds | Not supported | 14.1 all builds |
| 13.1 all builds | 13.1 all builds | 13.1 all builds | Not supported | 13.1 all builds | |
| 13.0 all builds | 13.0 all builds | 13.0 all builds | Not supported | ||
| 12.1–50.x (except TLS1.3-CHACHA20-POLY1305-SHA256) | 12.1–50.x (except TLS1.3-CHACHA20-POLY1305-SHA256) | 12.1–50.x | Not supported | ||
| TLS 1.1/1.2 | 14.1 all builds | 14.1 all builds | 14.1 all builds | 14.1 all builds | 14.1 all builds |
| 13.1 all builds | 13.1 all builds | 13.1 all builds | 13.1 all builds | 13.1 all builds | |
| 13.0 all builds | 13.0 all builds | 13.0 all builds | 13.0 all builds | ||
| 12.1 all builds | 12.1 all builds | 12.1 all builds | 12.1 all builds | ||
| ECDHE/DHE (Example TLS1-ECDHE-RSA-AES128-SHA) | 14.1 all builds | 14.1 all builds | 14.1 all builds | 14.1 all builds | 14.1 all builds |
| 13.1 all builds | 13.1 all builds | 13.1 all builds | 13.1 all builds | ||
| 13.0 all builds | 13.0 all builds | 13.0 all builds | 13.0 all builds | ||
| 12.1 all builds | 12.1 all builds | 12.1 all builds | 12.1 all builds | ||
| AES-GCM (Example TLS1.2-AES128-GCM-SHA256) | 14.1 all builds | 14.1 all builds | 14.1 all builds | 14.1 all builds | 14.1 all builds |
| 13.1 all builds | 13.1 all builds | 13.1 all builds | 13.1 all builds | 13.1 all builds | |
| 13.0 all builds | 13.0 all builds | 13.0 all builds | 13.0 all builds | ||
| 12.1 all builds | 12.1 all builds | 12.1 all builds | 12.1 all builds | ||
| SHA-2 Ciphers (Example TLS1.2-AES-128-SHA256) | 14.1 all builds | 14.1 all builds | 14.1 all builds | 14.1 all builds | 14.1 all builds |
| 13.1 all builds | 13.1 all builds | 13.1 all builds | 13.1 all builds | ||
| 13.0 all builds | 13.0 all builds | 13.0 all builds | 13.0 all builds | ||
| 12.1 all builds | 12.1 all builds | 12.1 all builds | 12.1 all builds | ||
| ECDSA (Example TLS1-ECDHE-ECDSA-AES256-SHA) | Not supported | 14.1 all builds | 14.1 all builds | 14.1 all builds | 14.1 all builds |
| Not supported | 13.1 all builds | 13.1 all builds | 13.1 all builds | 13.1 all builds | |
| Not supported | 13.0 all builds | 13.0 all builds | 13.0 all builds | ||
| Not supported | 12.1 all builds | 12.1 all builds | 12.1 all builds | ||
| CHACHA20 | Not supported | 14.1 all builds | 14.1 all builds | Not supported | 14.1 all builds |
| Not supported | 13.1 all builds | 13.1 all builds | Not supported | 13.1 all builds | |
| Not supported | 13.0 all builds | 13.0 all builds | Not supported | ||
| Not supported | Not supported | 12.1 all builds | Not supported |
Table 2 - Support on backend services:
| Protocol/Platform | MPX/SDX (N2) | MPX/SDX (N3) | VPX | MPX/SDX 14000** FIPS | MPX 5900/8900 MPX 15000-50G MPX 26000-100G |
|---|---|---|---|---|---|
| TLS 1.3 | NA | 14.1 all builds | 14.1 all builds | 14.1 all builds | 14.1 all builds |
| TLS 1.1/1.2 | 14.1 all builds | 14.1 all builds | 14.1 all builds | 14.1 all builds | 14.1 all builds |
| 13.1 all builds | 13.1 all builds | 13.1 all builds | 13.1 all builds | 13.1 all builds | |
| 13.0 all builds | 13.0 all builds | 13.0 all builds | 13.0 all builds | ||
| 12.1 all builds | 12.1 all builds | 12.1 all builds | 12.1 all builds | ||
| ECDHE/DHE (Example TLS1-ECDHE-RSA-AES128-SHA) | 14.1 all builds | 14.1 all builds | 14.1 all builds | 14.1 all builds | 14.1 all builds |
| 13.1 all builds | 13.1 all builds | 13.1 all builds | 13.1 all builds | ||
| 13.0 all builds | 13.0 all builds | 13.0 all builds | 13.0 all builds | ||
| 12.1 all builds | 12.1 all builds | 12.1 all builds | 12.1 all builds | ||
| AES-GCM (Example TLS1.2-AES128-GCM-SHA256) | 14.1 all builds | 14.1 all builds | 14.1 all builds | 14.1 all builds | 14.1 all builds |
| 13.1 all builds | 13.1 all builds | 13.1 all builds | 13.1 all builds | 13.1 all builds | |
| 13.0 all builds | 13.0 all builds | 13.0 all builds | 13.0 all builds | ||
| 12.1 all builds | 12.1 all builds | 12.1 all builds | 12.1 all builds | ||
| SHA-2 Ciphers (Example TLS1.2-AES-128-SHA256) | 13.1 all builds | 13.1 all builds | 13.1 all builds | 13.1 all builds | 13.1 all builds |
| 13.0 all builds | 13.0 all builds | 13.0 all builds | 13.0 all builds | ||
| 12.1 all builds | 12.1 all builds | 12.1 all builds | 12.1 all builds | ||
| ECDSA (Example TLS1-ECDHE-ECDSA-AES256-SHA) | Not supported | 14.1 all builds | 14.1 all builds | 14.1 all builds | 14.1 all builds |
| Not supported | 13.1 all builds | 13.1 all builds | 13.1 all builds | ||
| Not supported | 13.0 all builds | 13.0 all builds | 13.0 all builds | ||
| Not supported | 12.1 all builds | 12.1 all builds | 12.1 all builds | ||
| CHACHA20 | Not supported | 14.1 all builds | 14.1 all builds | Not supported | 14.1 all builds |
| Not supported | 13.1 all builds | 13.1 all builds | Not supported | 13.1 all builds | |
| Not supported | 13.0 all builds | 13.0 all builds | Not supported | ||
| Not supported | Not supported | 12.1 all builds | Not supported |
For the detailed list of ECDSA ciphers supported, see ECDSA Cipher Suites support.
- TLS-Fallback_SCSV cipher suite is supported on all appliances from release 10.5 build 57.x
- HTTP Strict Transport Security (HSTS) support is policy-based.
- All SHA-2 signed-certificates (SHA256, SHA384, SHA512) are supported on the front end of all appliances. In release 11.1 build 54.x and later, these certificates are also supported on the back-end of all appliances. In release 11.0 and earlier, only SHA256 signed-certificates are supported on the back end of all appliances.
- In release 11.1 build 52.x and earlier, the following ciphers are supported only on the front end of the MPX 9700 and MPX/SDX 14000 FIPS appliances:
- TLS1.2-ECDHE-RSA-AES-256-SHA384
- TLS1.2-ECDHE-RSA-AES256-GCM-SHA384 From release 11.1 build 53.x, and in release 12.0, these ciphers are also supported on the back end.
Perfect Forward Secrecy (PFS)
Perfect Forward Secrecy ensures protection of current SSL communications even if the session key of a web server is compromised at a later point in time.
Why do you need Perfect Forward Secrecy (PFS)?
An SSL connection is used to secure the data being passed between a client and a server. This connection begins with the SSL handshake that takes place between a client’s browser and the contacted web server. It is during this handshake that the browser and the server exchange certain information to arrive upon a session key which serves as a means to encrypt the data throughout the rest of the communication.
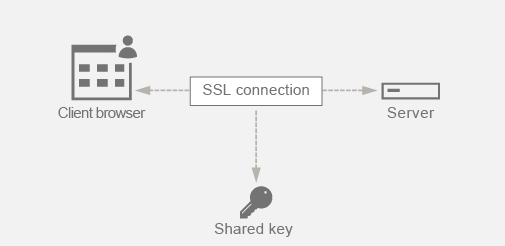
RSA is the most commonly used algorithm for key exchange. The browser uses the server’s public key to encrypt and send across the pre-master secret to a server. This pre-master secret is used to arrive at the session key. The problem in the RSA key exchange approach is that if an attacker manages to get hold of the server’s private key at any point in time in the future, then the attacker gets hold of the pre-master secret using which the session key can be obtained. This session key can now be used by the attacker to decrypt all the SSL conversations. As a result, your historical SSL communication that was secure earlier is no longer secure because the server’s stolen private key can be used to arrive at the session key and thus decrypt any saved historical conversation as well.
The need is to be able to protect the past SSL communication even if the server’s private key has been compromised. Configuring Perfect Forward Secrecy (PFS) helps address this issue.
How does PFS help?
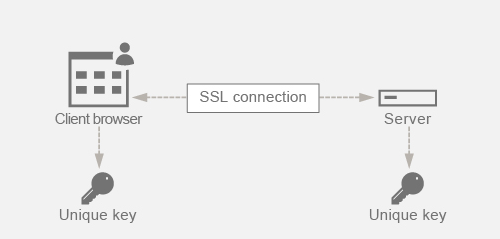
PFS protects the past SSL communication by having the client and server agree upon a new key for each session and keeping the computation of this session key a secret. It works on the basis that compromise of a server key must not result in compromise of the session key. Session key is derived separately at both ends and is never transferred over the wire. The session keys are also destroyed once the communication is complete. These facts ensure that even if someone gets access to the server’s private key, they would not be able to arrive at the session key. Therefore, they would not be able to decrypt the past data.
Explanation with example
Assume that we are using DHE for attaining PFS. The DH algorithm ensures that even though a hacker gets hold of the server’s private key, the hacker cannot arrive at the session key. The reason is that the session key and the random numbers (used to arrive at the session key) are kept secret at both ends and never exchanged over the wire. PFS can be achieved by using the Ephemeral Diffie-Hellman key exchange which creates new temporary keys for each SSL session.
The flip side of creating a key for each session is that it requires extra computation. However, this issue can be overcome by using the Elliptic Curve which has smaller key sizes.
Configure PFS on NetScaler appliance
PFS can be configured on a NetScaler by configuring DHE or ECDHE ciphers. These ciphers ensure that the secret session key created is not shared on the wire (DH algorithm) and that the session key remains alive only for a short time (Ephemeral). Both the configurations are explained in the following sections.
Note: Using ECDHE ciphers instead of DHE makes the communication more secure with smaller key sizes.
Configure DHE by using the GUI
- Generate a DH key. a. Navigate to Traffic Management > SSL > Tools. b. Click Create Diffie Helman (DH) Key. Note: Generating a 2048-bit DH key can take up to 30 minutes.
- Enable DH Param for the SSL virtual server and attach the DH key to the SSL virtual server. a. Navigate to Configuration > Traffic Management > Virtual Servers. b. Select the virtual server on which you want to enable DH. c. Click Edit, click SSL Parameters, and click Enable DH Param.
- Bind the DHE ciphers to the virtual server. a. Navigate to Configuration > Traffic Management > Virtual Servers. b. Select the virtual server on which you want to enable DH and click the pencil icon to edit. c. Under Advanced Settings, click the plus icon next to SSL Ciphers and select the DHE cipher groups and click OK to bind. Note: Ensure that the DHE ciphers are at the top of the cipher list bound to the virtual server.
Configure ECDHE by using the GUI
- Bind the ECC curves to the SSL virtual server. a. Navigate to Configuration > Traffic Management > Load Balancing > Virtual Servers. b. Select the SSL virtual server which you want to edit, click ECC Curve and click Add Binding. c. Bind the required ECC curve to the virtual server.
- Bind the ECDHE ciphers to the virtual server. a. Navigate to Configuration > Traffic Management > Virtual Servers and select the virtual server on which you want to enable DH. b. Click Edit > SSL Ciphers and select the ECDHE cipher groups and click Bind. Note: Ensure that the ECDHE ciphers are at the top of the cipher list bound to the virtual server.
Note: For each case verify that the NetScaler appliance supports the ciphers you would like to use for the communication.
Configure PFS using an SSL profile
Note: Option to configure PFS (cipher or ECC) using an SSL profile is introduced from 11.0 64.x release onwards. Ignore the following section if on older versions.
To enable PFS using an SSL profile, a similar configuration (as explained in earlier configuration sections) needs to be done but on the SSL profile instead of directly configuring on a virtual server.
Configure PFS using an SSL profile by using the GUI
- Bind the ECC curves and the ECDHE ciphers on the SSL profile. Note: ECC curves are already bound by default to all the SSL profiles. a. Navigate to System > Profiles > SSL Profiles and choose the profile you want to enable PFS on. b. Bind the ECDHE ciphers.
- Bind the SSL profile to the virtual server. a. Go to Configuration > Traffic Management > Virtual Servers and select the virtual server. b. Click the pencil icon to edit the SSL profile. c. Click OK and click Done.
Configure PFS using SSL using the CLI
At the command prompt, type:
-
Bind ECC curves to the SSL profile.
The official version of this content is in English. Some of the Cloud Software Group documentation content is machine translated for your convenience only. Cloud Software Group has no control over machine-translated content, which may contain errors, inaccuracies or unsuitable language. No warranty of any kind, either expressed or implied, is made as to the accuracy, reliability, suitability, or correctness of any translations made from the English original into any other language, or that your Cloud Software Group product or service conforms to any machine translated content, and any warranty provided under the applicable end user license agreement or terms of service, or any other agreement with Cloud Software Group, that the product or service conforms with any documentation shall not apply to the extent that such documentation has been machine translated. Cloud Software Group will not be held responsible for any damage or issues that may arise from using machine-translated content.
DIESER DIENST KANN ÜBERSETZUNGEN ENTHALTEN, DIE VON GOOGLE BEREITGESTELLT WERDEN. GOOGLE LEHNT JEDE AUSDRÜCKLICHE ODER STILLSCHWEIGENDE GEWÄHRLEISTUNG IN BEZUG AUF DIE ÜBERSETZUNGEN AB, EINSCHLIESSLICH JEGLICHER GEWÄHRLEISTUNG DER GENAUIGKEIT, ZUVERLÄSSIGKEIT UND JEGLICHER STILLSCHWEIGENDEN GEWÄHRLEISTUNG DER MARKTGÄNGIGKEIT, DER EIGNUNG FÜR EINEN BESTIMMTEN ZWECK UND DER NICHTVERLETZUNG VON RECHTEN DRITTER.
CE SERVICE PEUT CONTENIR DES TRADUCTIONS FOURNIES PAR GOOGLE. GOOGLE EXCLUT TOUTE GARANTIE RELATIVE AUX TRADUCTIONS, EXPRESSE OU IMPLICITE, Y COMPRIS TOUTE GARANTIE D'EXACTITUDE, DE FIABILITÉ ET TOUTE GARANTIE IMPLICITE DE QUALITÉ MARCHANDE, D'ADÉQUATION À UN USAGE PARTICULIER ET D'ABSENCE DE CONTREFAÇON.
ESTE SERVICIO PUEDE CONTENER TRADUCCIONES CON TECNOLOGÍA DE GOOGLE. GOOGLE RENUNCIA A TODAS LAS GARANTÍAS RELACIONADAS CON LAS TRADUCCIONES, TANTO IMPLÍCITAS COMO EXPLÍCITAS, INCLUIDAS LAS GARANTÍAS DE EXACTITUD, FIABILIDAD Y OTRAS GARANTÍAS IMPLÍCITAS DE COMERCIABILIDAD, IDONEIDAD PARA UN FIN EN PARTICULAR Y AUSENCIA DE INFRACCIÓN DE DERECHOS.
本服务可能包含由 Google 提供技术支持的翻译。Google 对这些翻译内容不做任何明示或暗示的保证,包括对准确性、可靠性的任何保证以及对适销性、特定用途的适用性和非侵权性的任何暗示保证。このサービスには、Google が提供する翻訳が含まれている可能性があります。Google は翻訳について、明示的か黙示的かを問わず、精度と信頼性に関するあらゆる保証、および商品性、特定目的への適合性、第三者の権利を侵害しないことに関するあらゆる黙示的保証を含め、一切保証しません。
ESTE SERVIÇO PODE CONTER TRADUÇÕES FORNECIDAS PELO GOOGLE. O GOOGLE SE EXIME DE TODAS AS GARANTIAS RELACIONADAS COM AS TRADUÇÕES, EXPRESSAS OU IMPLÍCITAS, INCLUINDO QUALQUER GARANTIA DE PRECISÃO, CONFIABILIDADE E QUALQUER GARANTIA IMPLÍCITA DE COMERCIALIZAÇÃO, ADEQUAÇÃO A UM PROPÓSITO ESPECÍFICO E NÃO INFRAÇÃO.